本文为摘录(或转载),侵删,原文为: https://medium.com/flat-pack-tech/threat-modeling-as-code-f3555f5d9024
这个图解释了它为什么叫 C4:
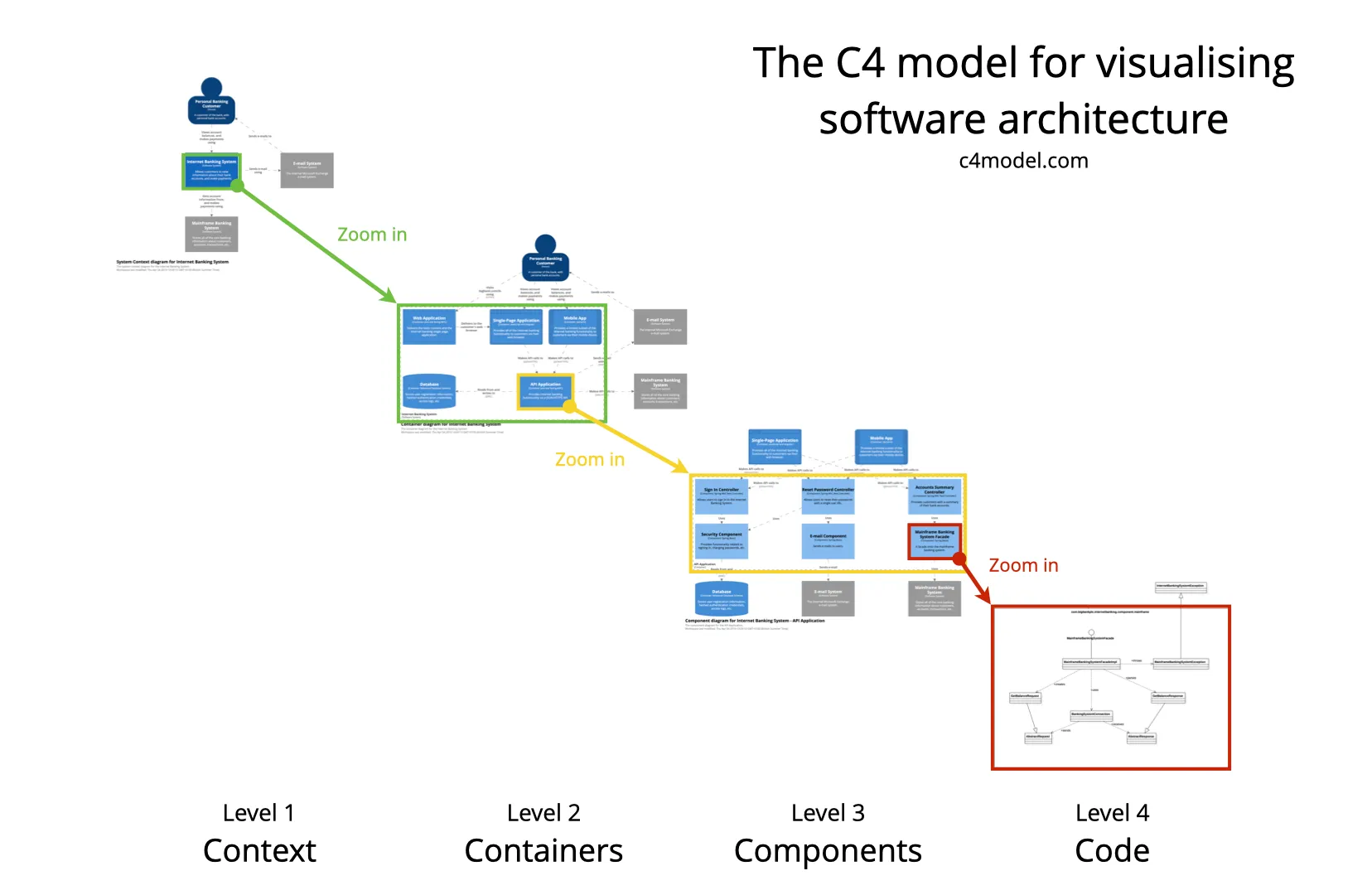
Figure 1: C4
1 Stop drawing, Start coding
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| @startuml
!include <C4/C4_Container.puml>
Person(person1, "Person 1","")
System(system1, System 1, "Description System 1")
System_Boundary(bounday1, "Cloud Boundary 1") {
Container(container1, Container 1, "Description Container 1")
ContainerDb(database1, Database 1, "Description Database 1")
}
Rel(person1, container1, Uses, "HTTPS Request with JWT token")
Rel(container1, system1, Uses, "Request to external API with Access Token")
Rel(container1, database1, "Queries", "Data information per user identifier")
@enduml
|
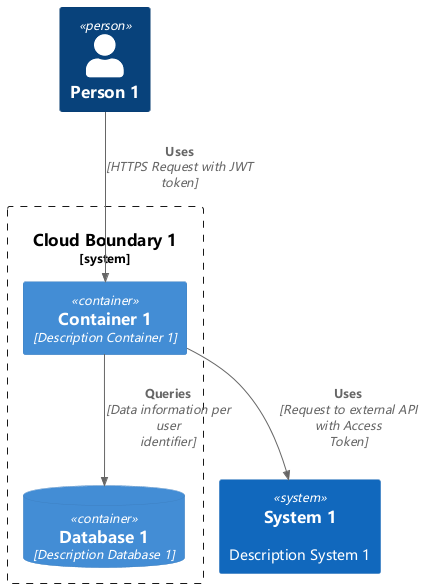
Figure 2: simple c4
In this example, we have used C4 Container level with the following entities:
- Person: Developers, end-users or attackers.
- System: External platforms.
- System Boundary: Cloud environments.
- Container: Our backend/frontend application.
- ContainerDb: Databases.
2 Threat modeling and beyond
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| @startuml
!include <C4/C4_Container.puml>
!include iuml_files/stride.puml
Person(person1, "Person 1","")
System(system1, System 1, "Description System 1")
System_Boundary(bounday1, "Cloud Boundary 1") {
Container(container1, Container 1, "Description Container 1")
ContainerDb(database1, $Stride("RI")\n===Database 1, "Description Database 1")
}
Rel(person1, container1, $AggregatedRisk("R1") Uses, "HTTPS Request with JWT token")
Rel(container1, system1, $AggregatedRisk("R2") Uses, "Request to external API with Access Token")
Rel(container1, database1, "Queries", "Data information per user identifier")
$RiskTable() [
=== Aggregated Risks
----
$AggregatedRisk("R1") Details of aggregated risk number 1.
----
$AggregatedRisk("R2") Details of aggregated risk number 2
]
@enduml
|
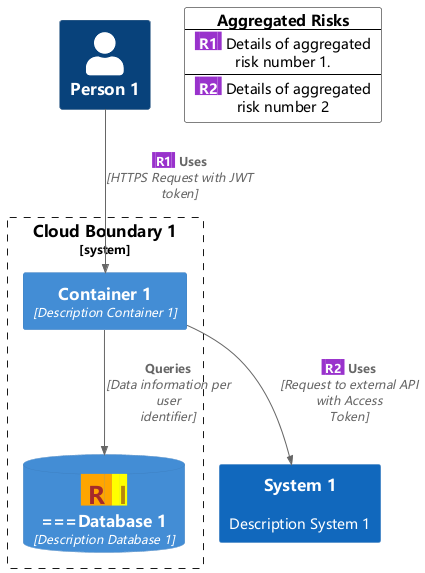
Figure 3: stride model
通过这种方法,我们正在将信任边界从经典的威胁建模扩展到任何类型的系统表示。然而,我们并没有提供一种清晰的方法来表示模型中每个组件的信任和价值,因此我们需要创建一个信任:价值比率。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| @startuml
!include <C4/C4_Container.puml>
!include iuml_files/stride.puml
Person(person1, "Person 1","")
System(system1, <size:5>$TrustValueRatio("1:3")\n===System 1, "Description System 1")
System_Boundary(bounday1, "Cloud Boundary 1") {
Container(container1, <size:5>$TrustValueRatio("2:5")\n===Container 1, "Description Container 1")
ContainerDb(database1, <size:5>$TrustValueRatio("2:5")\n$Stride("RI")\n===Database 1, "Description Database 1")
}
Rel(person1, container1, $AggregatedRisk("R1") Uses, "HTTPS Request with JWT token")
Rel(container1, system1, $AggregatedRisk("R2") Uses, "Request to external API with Access Token")
Rel(container1, database1, "Queries", "Data information per user identifier")
$RiskTable() [
=== Aggregated Risks
----
$AggregatedRisk("R1") Details of aggregated risk number 1.
----
$AggregatedRisk("R2") Details of aggregated risk number 2
]
@enduml
|
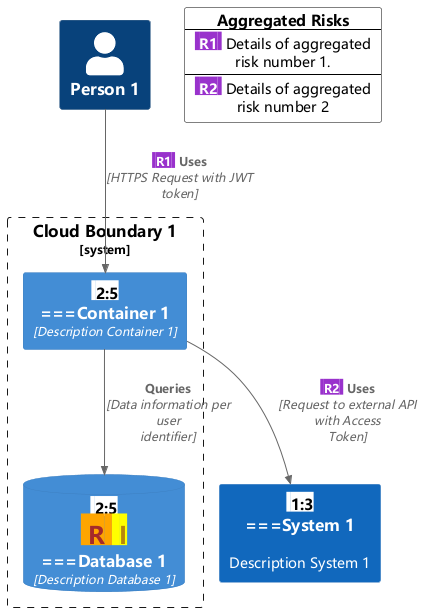
Figure 4: stride-with-trust-value
3 REFERENCE:



